
Securing the Internet of Everything
When you think about the Internet of Things (IoT), fitness trackers or smart thermostats might be among the first things that come to mind. They’re designed to seamlessly connect and make our lives more convenient and efficient.
But IoT technology isn’t just useful on a personal level. The ‘Things’ in question could be anything. Dams, dishwashers, aircraft, and Alexa speakers all count – as long as they are embedded with sensing, computing, and communication hardware; and linked to software that enables them to collect and send data, and automatically perform actions. For engineers, this means unprecedented access to measurements of the systems, devices, vehicles, and structures they design and build.
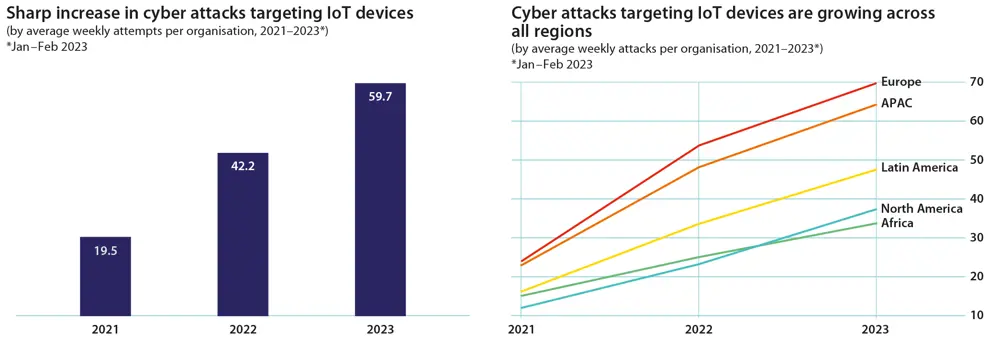
More devices equals more cyberattacks
Statista estimates that there are already about 17 billion IoT devices in the world. Some analysts believe there could be 42 billion IoT devices by 2025. With this explosion in their numbers, plus the many different types of application that now exist, security and privacy have become a pressing issue.
Indeed, cyber incidents involving IoT devices are constantly on the rise, highlighting the urgency with which we need to address security vulnerabilities and protect user data. For example, while a Peloton fitness bike might seem harmless enough, in 2021, cybersecurity experts claimed they had found a way that hackers could gain access to monitor users via its camera and steal sensitive data. Clearly, this issue demands our attention.

Engineers play a crucial role in designing smart and sustainable systems, making our critical infrastructure – transportation systems, communication networks, and power grids – ever more capable and efficient. IoT is at the heart of this evolution.
For example, IoT devices could help track the complete journey of energy until it arrives in our homes, from its generation to distribution. A smart grid enabled by IoT could help to balance supply and demand to avoid disruption as well as overproduction of energy. At the same time, it could also inform other linked infrastructure, such as water systems. For example, when demand on the grid is high, tasks such as pumping water into reservoirs could be automatically deferred, as it doesn’t have to run at a specific time.
However, as with personal devices, networking our interconnected critical systems and processes brings heightened cybersecurity threats, which we must address now. For example, cyberattacks are a growing concern for energy companies, and IoT sensors networked into the grid could provide attackers with another way in if not secured effectively.
Privacy, ethics, trust, and security
The greater convenience afforded by IoT also comes at the price of increased data collection and sharing. Such a practice may infringe upon our privacy, personal safety, or access to services. For example, if vehicle data is shared with insurers, their assessments may account for an increased risk and thus a higher price for car insurance.
Moreover, many users of domestic IoT do not realise their devices are sending patterns of information that can say a lot about their lives, and their data are brokered at marketplaces to marketing companies worldwide.
IoT devices are already in many of our homes, workplaces, and public spaces. As their numbers and our uses for them grow, it will become more and more difficult to opt out of data collection in situations when we may not want to be monitored.
Many users of domestic IoT do not realise their devices are sending patterns of information that can say a lot about their lives, and their data are brokered at marketplaces to marketing companies worldwide.
To address these issues, researchers are focusing their efforts on developing so-called privacy-enhancing technologies (PET). These aim to maximise the benefits made possible by data collection, while reducing potential harms. One well-known example of a PET is onion routing – a way of anonymising user data online.
It is not only privacy (individual control over data shared) that is important here. Even voluntarily sharing too much information can make people vulnerable and organisations unsafe. For example, sensitive inferences can be drawn from combinations of apparently unconnected devices that collect seemingly innocuous metadata (for instance, the time and date data is created).
Hence, data must be collected and processed responsibly. Cybersecurity measures must be robust and follow international principles and national regulations for ethical and legal conduct. Importantly, compliance should be monitored to preserve human rights and personal dignity.
Responsible digital citizens
We are constantly reminded that new and emerging technologies, with all their promise, can have unforeseen consequences. For example, social networks, generative AI, and smartphones have all played a role in the contagious spread of misinformation.
As a new technology, IoT could be dangerous if it enables harm to critical infrastructure such as our water services, healthcare or political systems, or individual wellbeing – from sleep to mental health. IoT has already caused concern through its role in facilitating domestic violence, through eavesdropping with smart speakers and stalking with IoT tracking devices, for example. It’s critical that experts worldwide work in partnership with users to develop tools that enhance digital literacy and ‘cyberhygiene’; and teach the next generation how to use technologies safely and smartly.
Engineers will be at the heart of addressing these challenges and must be ready to work with colleagues across disciplines, including design and behavioural sciences as well as computing, communications and software.
Protecting our digital world
The ever-growing world of interconnected IoT devices will require many different talents and types of innovative thinker to solve the technical, social, cyber, and physical challenges that lie ahead.
Engineers will be at the heart of addressing these challenges and must be ready to work with colleagues across disciplines, including design and behavioural sciences as well as computing, communications and software.
For example, more robust cybersecurity standards will require encryption experts, but also social scientists and user-centric designers. The latter can investigate how humans can interact safely – or indeed, unsafely – with devices. Collaborative efforts from researchers in universities and industry across many disciplines will be essential to creating a safe and trusted IoT environment that benefits people.
Engineers at all career stages are invited to join this grand challenge to release the transformative power of IoT. Your contributions can make a significant impact, either by staying informed, promoting awareness, or advancing the science and engineering associated with IoT. Together, we can help build a more secure and connected future.
***
With thanks to Gideon Ogunniye, Joe Bourne, Jeremy D McK. Watson CBE FREng, Rachel Cooper OBE, Julie A McCann, David De Roure, Tim Watson
***
This article has been adapted from "Securing the Internet of Everything", which originally appeared in the print edition of Ingenia 96 (September 2023).
Contributors
The PETRAS National Centre of Excellence for IoT Systems Cybersecurity – a seven-year, EPSRC-funded partnership of 24 universities – connects many researchers across social and physical science disciplines with industry and government to tackle these issues in theoretical, practical, and impactful ways. Jeremy D McK. Watson CBE FREng is the centre’s the Director and Principal Investigator.
Keep up-to-date with Ingenia for free
SubscribeRelated content
Electricals & electronics

Accelerometers
Used in earthquake measurements, laptops, planes and even in stargazing apps, today’s accelerometers are much smaller than when they were first developed in 1927. Find out how they detect movement and vibration.

How to maximise loudspeaker quality
Ingenia asked Dr Jack Oclee-Brown, Head of Acoustics at KEF Audio, to outline the considerations that audio engineers need to make when developing high-quality speakers.

Cable fault locator
The winner of the Institute of Engineering and Technology’s 2014 Innovation Award was EA Technology’s CableSnifferTM, which uses a probe and chemical sensing technology to identify faults, saving energy companies millions of pounds each year.

High speed evolution
In December 2010, Eurostar International Ltd awarded a contract for 10 new high speed trains to Siemens. The company has used a system developed over decades to maximise the performance and passenger-carrying ability of its 320km/h trains.
Other content from Ingenia
Quick read

- Environment & sustainability
- Opinion
A young engineer’s perspective on the good, the bad and the ugly of COP27

- Environment & sustainability
- Issue 95
How do we pay for net zero technologies?
Quick read

- Transport
- Mechanical
- How I got here
Electrifying trains and STEMAZING outreach

- Civil & structural
- Environment & sustainability
- Issue 95